I run a Jenkins server to build projects like the Arietta G25 Kernel and Banana Pi Kernel.
I also run a FreeIPA server for central authentication and user rights management. I’m not an expert on LDAP and Kerberos, which is why I like FreeIPA because it allows me to manage these without requiring that I be an LDAP or Kerberos demigod.
So, here’s how to configure Jenkins to authenticate against FreeIPA. You will need to install the Jenkins LDAP plugin before proceeding.
The plugin can be installed by clicking on: Manage Jenkins -> Manage Plugins -> Available -> Search “LDAP Plugin”
On the FreeIPA server create an LDIF file to define an unprivileged user to read the LDAP tree. The FreeIPA LDAP server does not appear to support anonymous binds. I recommend the makepasswd program to generate the user password.
-bash-4.2$ cat jenkins.ldif dn: uid=jenkins,cn=sysaccounts,cn=etc,dc=watchmysys,dc=com changetype: add objectclass: account objectclass: simplesecurityobject uid: jenkins userPassword: 7b1yYzNINU passwordExpirationTime: 20380119031407Z nsIdleTimeout: 0
To create the user you need to apply this LDIF to LDAP:
ldapmodify -h ipa.watchmysys.com -p 389 -x -D "cn=Directory Manager" -W -f jenkins.ldif
When the LDAP plugin is installed go back to the “Manage Jenkins” menu, click on “Configure Global Security” and “Enable security”
Next select “Security Realm” -> “LDAP”, and configure the settings for your IPA server as described below:
Server: ldaps://ipa.watchmysys.com root DN: dc=watchmysys,dc=com User search base: cn=users,cn=accounts User search filter: (objectClass=inetOrgPerson)(objectClass=posixAccount)(uid=%u) Group search filter: jenkins Manager DN: uid=jenkins,cn=sysaccounts,cn=etc,dc=watchmysys,dc=com Manager password: 7b1yYzNINU Display Name LDAP attribute: displayname Email Address LDAP attribute: mail
You may want to choose ldap:// instead of ldaps:// during your testing. I found it useful to run tcpdump between my Jenkins server and IPA server to diagnose authentication failures.
In FreeIPA create a role for Jenkins users:
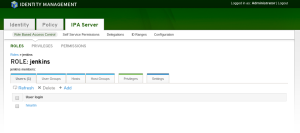
Here is what the corresponding LDAP object is:
# jenkins, roles, accounts, watchmysys.com dn: cn=jenkins,cn=roles,cn=accounts,dc=watchmysys,dc=com objectClass: groupofnames objectClass: nestedgroup objectClass: top cn: jenkins description: Jenkins administrators member: uid=hmartin,cn=users,cn=accounts,dc=watchmysys,dc=com
I decided that all Jenkins users should be allowed to administer once logged in. You may decide to implement a more complex security system with different privilege levels.
Save the changes. You will be unable to administer Jenkins without logging in now. Jenkins will update config.xml in its home with the new security settings:
<useSecurity>true</useSecurity> <authorizationStrategy class="hudson.security.FullControlOnceLoggedInAuthorizationStrategy"/> <securityRealm class="hudson.security.LDAPSecurityRealm" plugin="[email protected]"> <server>ldaps://ipa.watchmysys.com</server> <rootDN>dc=watchmysys,dc=com</rootDN> <inhibitInferRootDN>false</inhibitInferRootDN> <userSearchBase>cn=users,cn=accounts</userSearchBase> <userSearch>(objectClass=inetOrgPerson)(objectClass=posixAccount)(uid=%u)</userSearch> <groupSearchFilter>jenkins</groupSearchFilter> <groupMembershipStrategy class="jenkins.security.plugins.ldap.FromGroupSearchLDAPGroupMembershipStrategy"> <filter></filter> </groupMembershipStrategy> <managerDN>uid=jenkins,cn=sysaccounts,cn=etc,dc=watchmysys,dc=com</managerDN> <managerPasswordSecret>bdV4rdfP9sQ1JTsDfJYGQSRvqYtsSafFdVLYwiuv6nTyiaAnfIwxeC2GNfQmy0dfs</managerPasswordSecret> <disableMailAddressResolver>false</disableMailAddressResolver> <displayNameAttributeName>displayname</displayNameAttributeName> <mailAddressAttributeName>mail</mailAddressAttributeName> </securityRealm>
If you cannot login to Jenkins using your LDAP username and password then remove the above lines from your config.xml and restart Jenkins. Jenkins will revert back to the default policy of anonymous users are admins.
If your user is not in the Jenkins role on the FreeIPA server you will not be able to login.
You should now have LDAP-based authentication working in Jenkins. You now have all the benefits of central user management in Jenkins, enjoy!
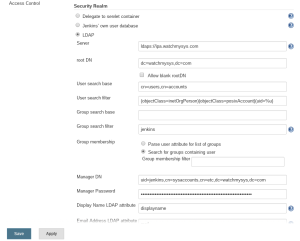
hello I apply all you conf ,but not success ,need your help
Hi, this post is quite old, so I doubt the configuration mentioned here is still working.
I’m not using Jenkins anymore, so hopefully you can find someone else who’s written instructions on how to integrate newer versions of Jenkins with FreeIPA/OpenLDAP.