A few years ago we looked at iRMC S4 on the Fujitsu TX140 S2. iRMC S4 provides typical remote management features that you would expect to find in a BMC: remote power control, sensor monitoring and alerting, hardware inventory, and boot order over-ride/selection. Some additional features like the remote KVM and remote media require a license key.
Licensed IPMI features are not new and other vendors, such as Supermicro, have had their IPMI license reverse engineered.
Fujitsu are a somewhat niche vendor when it comes to servers, and to date I am not aware that anyone has publicly reverse engineered the iRMC S4 license.
They say a picture is worth a thousand words, so we will start with a diagram
An iRMC S4 license has four distinct fields
- Header/magic: 4 bytes (
iRMC) - Features to be enabled by the license (bitmask): 4 bytes
- Type of license (temporary or permanent): 4 bytes
- CRC32 of the system serial number: 4 bytes
The above data is encrypted using AES-128, and the output is base32 encoded with hyphens every 4 characters.
For example, here is an iRMC S4 license (enabling KVM and remote media) for an RX chassis with the serial number YLNS012345:
ZKAF-Z5EG-PL5G-6GFR-YEG6-CKGM-KQ
And the actual license contents:
69524d43 0300000 0ffffff05 2e4dbb51
Licensed features in iRMC S4 include:
- Remote KVM
- Remote media
- eLCM
Feature bit 1 is for KVM, bit 2 remote media, and bit 3 seems to be for eLCM (eLCM appears to only be available on some models).
Back in 2014, Fujitsu changed the iRMC S4 licensing to be “node-locked”, which means that a license is tied to a specific server and cannot be transferred. The installation of a volume license is not possible after 2015-01-01 00:00:00.
iRMC S4 tracks the “Power on Hours (PoH)” of the chassis, and it appears that there is the capability to generate a temporary license which will expire after a certain number of Power on Hours is reached, probably to provide customers with time to evaluate the value proposition of purchasing iRMC licenses.
If you are reading this, then you are probably not interested in generating temporary licenses. Setting the field to 0xffffff00 for a TX chassis and 0xffffff05 for an RX chassis will result in a permanent license.
Now that we have covered the fields in an unencrypted iRMC S4 license, it will be obvious that the example license ZKAF-Z5EG-PL5G-6GFR-YEG6-CKGM-KQ is not simply the base32 encoded binary license data.
Unlike Supermicro, Fujitsu use a static HMAC message and key to create an HMAC-SHA1 hash, the first 16 bytes of which are used as the key for AES-128. The AES encrypted data is then base32 encoded and the output is the iRMC license you install via the web interface.
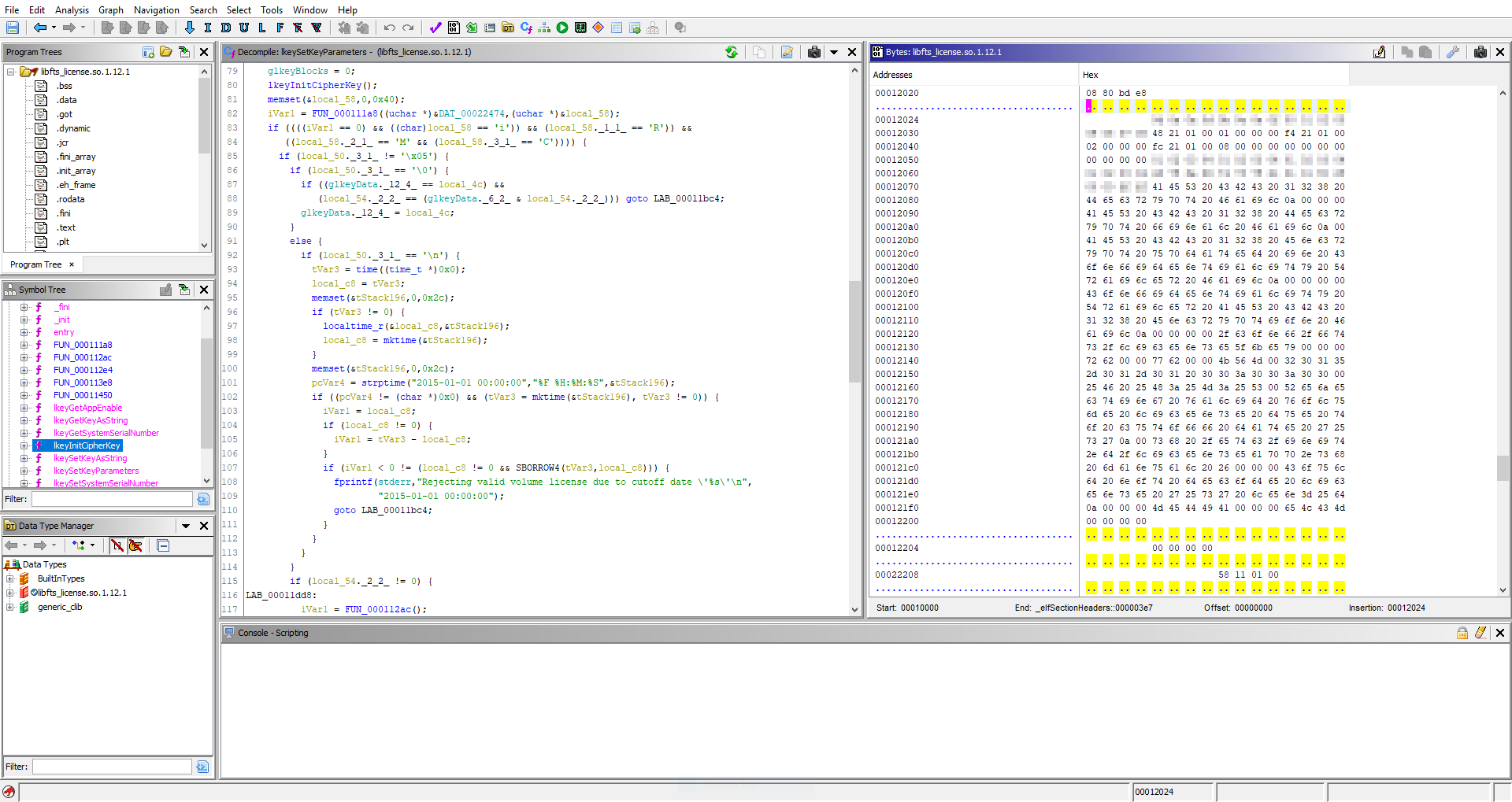
I will not be disclosing Fujitsu’s HMAC key and AES IV here, but suffice to say you can download and unpack the iRMC firmware from Fujitsu and find the values in /usr/local/lib/libfts_license.so.1.12.1. Thanks Fujitsu!
For anyone interested in reverse engineering the iRMC S4 license validation themselves:
- the HMAC key and message are used in
lkeyInitCipherKeyinlibfts_license - the AES IV is used in
decrypt_with_licenseinlibfts_license
Anyone looking for a simpler solution, a proof-of-concept for python is here. Note that you need to provide the correct HMAC/AES values obtained from libfts_license, you do not need Ghidra for this, you can do it with a simple hexdump utility.
If you want to investigate the exported license (using “iRMC S4” -> “Save Configuration” -> “Include License Information”), here is a validation script.
To anyone wondering, the license logic from iRMC S4 is not applicable to older iRMC platforms such as iRMC S2 or iRMC S3.
However, the license logic appears to be unchanged between iRMC S4 and S5. Hardware with iRMC S5 is too expensive to justify purchasing to verify this, but maybe someone will leave a comment as to whether the license logic described here is still applicable to iRMC S5.
Edit: An anonymous reader has written to say that the logic is unchanged for iRMC S5/S6 ✨


Great article and research.
I for once cant seem to find the file you mention , when downloading the fujitsu firmware. Are the files on the request only open source, or is there a way to extract them from the .bin file of the firmware?
If i download and create the pen, can´t find it there either.
Run
binwalk -e FTS_TX140S2D3239iRMCKronos4FirmwareUpdatefo_TX140S20960Fsdr0344_1233853.BINand then extract the cramfs (you’ll needcramfs-tools).Thanks Martin for that great article,
can´t find HMAC and AES IV data in ibfts_license.so.1.12.1 🙁
For legal reasons, I will not be disclosing the values.
But the Ghidra screenshot includes a hexdump that you might find useful 😉
Edit: There are three 16 byte values you need to obtain from the library. Addresses shown in Ghidra hex view are offset by +0x1000 from what you would see when using
hexdump. If you look at thecodein the post, there is a clue about part of the HMAC 😉Really great work.
I am in the same boat, unfortunately.
Even studying your screenshot very thoroughly, I can not deduct which values to extract from libfts_license (only have a hex editor at hand). As I understand, the python script requires a 16 byte HMAC key, a 64 byte HMAC msg (or a 16 byte sequence that is multiplied “* 4”?), and a 16 Byte AES IV value.
In the screenshot I can only see a censored 16 byte sequence and a censored 32 byte sequence (which i can find in the file)… Tried all sorts of combinations, but never got a working serial number. 🙁
Any suggestion on which byte sequence to map on which script variable would be appreciated.
For everyone as dumb as me (posted before, but my post isnt released until now from author) two hints:
HEX for the script in the style of:
\x00\x01\x02
NOT(!) like this:
00 01 02
000102
Maybe that’s not clear for everyone.
Than just rotate the keys a little bit trough the possible three fields and remember: The Company always has a good message for you and a key clearly could just contain numbers, even if AES isn’t near as dead as some people believe. 😉
The message by that company is indeed a good hint!
It has been a great adventure, one of the best catch the treasure i’ve ever done and FireTiger gave me the last tip, thank you guys you’re the best!
Tips:
– decompress the bin
– find the file
– use the reverse tool
– look closely the image
– read the FireTiger comment
– pip install pycryptodome to let the python do the job and avoid errors
In june 2024 it takes nearly an entire afternoon to understand and make everything work but what a satisfaction read “permanent license key installed”
Extremely impressive work! I have no idea how you figured all of this out.
KVM_Media_eLCM working great on Fujitsu TX1320 M3.
The video redirection didn’t want to work using the Java WebStart avr.jnlp file (black screen), but if you go to Console Redirection > Video redirection and turn on the HTML5 player, you can see the video output from the machine just fine (not sure if this is a feature that appears only after IPMI fimware update).
Took me a while to figure out where to put what due to the riddle form, but it’s all been more rewarding in the end thanks to that 🙂
Thank you so much!
I found the values from your screenshot. Do I need more?
I am confused that the blurred values are longer than 16 characters? 🙁
There are three 16 byte values you need to obtain from the library.
Two of the 16 byte values happen to be adjacent to each other, which is why there are more than 16 bytes blurred.
Thanks for your work. With your screenshot was easy. Now I have two servers with KVM_Media.
I somehow struggle to understand where the begin of the relevant data is… any hint for the three address starts?
Python script worked with my tx1320 m2 MB. Many thanks for the posts and hints.
Okay, maybe a very dumb question:
I found the HEX-values, extracted them and then I got some errors. Maybe I don’t get the right meaning of the HMAC-/AES-HEX-values in the script (or the right fields to the right input). First of all, putting HEX to script directly from HEX-Editor is a bad idea -> spaces collides with len(). So I removed them.
Next I stripped the 0s out of the HEX, worked for two of three fields, but the one with the nice companies name statement doesn’t work obviously, cause of no leading 0. Do I get something totally wrong here? Should that HEX-field be cut into half?
A short hint would be very nice.
Than just rotate the keys a little bit trough the possible three fields and remember: The Company always has a good message for you and a key clearly could just contain numbers, even if AES isn’t near as dead as some people believe.
This sentence is very important, I have successfully found the secret key 😉
As a complete noob coming into this, I thought you might have been crazy. Thanks for the poignant message, though. Out the other end, it makes perfect sense. (although I might now be a little crazy).
Tested working KVM MEDIA and eLCM on TX1320 M3 on iRMC 9.08F.
Thanks for the elaboration on this! In a test environment for educational purposes only, this works with a Fujitsu TX1320 M3 (iRMC S4 Firmware version 9.08F) and with KVM_Media (but not with KVM_Media_eLCM) using the Pyhton script (GitHub: halmartin/irmc_s4.py “Fujitsu iRMC S4 PoC”, linked in the article).
After updating to iRMC S4 Firmware 9.69F (Base: 9.69.F), the licenses still persist/work.
One interesting point: I observed a different license key in the exported XML than the one entered (using “iRMC S4” -> “Save Configuration” -> “Include License Information”).
If one does not get the combination/assignment of the three extracted 16 Byte hex values (blurred in the screenshot) right, try all 6 permutations. You can also check your script by feeding/comparing it with input/output values given here (article), which must match.
Of course the hex values must be noted correctly in Python, e.g.:
HM___K_Y = b”\x01\x01….\x01″ (mod edit: example values, do not interpret as a hint)
> One interesting point: I observed a different license key in the exported XML than the one entered (using “iRMC S4” -> “Save Configuration” -> “Include License Information”).
Yes, this can happen. I added a link to a validator in the post which will tell you which features are licensed as well as dumping the raw license as hex. You can input your exported license, and compare to the above description of the license fields to see what’s changed.
Thanks for this little riddle! Got it after some time 🙂
I had problems with the Crypto Module (Module not found) on Windows. I couldn’t install the pycrypto modul through pip because of missing C++ Build Tools but pycryptodome did work.
Hello. Thank you very much for the tutorial. By any chance, do you know the iRMC S2 license logic? Or could you steer me into the right direction, how to obtain it? Thanks
Earlier versions of iRMC (S2/S3) are based on an RTOS, and I do not have any knowledge of the license logic used in these. You can download the complete firmware from Fujitsu’s support website, and a disassembler like Ghidra or IDA should get you started.
How does the python script get the serial number part of the License code?
I’ve been trying to get mine to work but i just cant seem to get it to work 🙁
I have the hmac and aes keys but how do i add my own serial number to the script
It is provided as an argument at runtime:
./irmc_s4.py YLNS012345Found that this didn’t work on a TX1330 M2 – however changing the Chassis type to
0xFFFFFF01 and it was accepted.
Interesting! Would you be able to export your installed license and email it to me so I can take a look at the decrypted contents?
Resolving the words riddle was the difficult part 🙂
Hello
How can i open the libfs in ghiada ?
what language ?
i always get error “xml document structures must start and end within the same entity”
Awesome work ! Just wanted to say hi and thanks. With your blog post and the script, i am now able to use kvm_media_eLCM license permanently activated in rx 2530 m2 with iRMC S4 Firmware 9.69F. I had to fetch the ubuntu 16 to install the necessary packages for binwalk. Then used hd command for the hexdumb. Then it was all clear to read. One should also think about the possible 6 permutations just in case.
Took me a few tries but I got it, now I have iRMC S4 activated on my TX1320 M2, thanks!
Thank you for an interesting quest in finding and creating the correct licence, I really enjoyed the data mining (I’m not an expert but managed it in 3 hours with a great result at the end)
Thank you for your effort!
I’m dumb, so I had to spend 2 evenings in Ghidra and go through code step-by-step before I found the answer and realized how many hints you already left in your post.
FYI: mine is TX140S2 with D3239 motherboard, clearly TX chassis, but using “-t RX -f KVM_Media_eLCM” options I can get eLCM actiated.
Thank you again,
Firstly, a very nice and useful description of the Fujitsu iRMC S4 License Model’s operation.
I can also confirm that the proof-of-concept works flawlessly on the RX13330M1.
Thank you once again for your effort and dedication you put into this.
Additionally, thanks to all other commentators for their valuable insights :).
Everything is fine, I managed to activate the RX1330M1, thank you Martin
Unfortunately, it’s not working on my TX 140 S2 🙁
The py-script works without problems, but the iRMC said that the license-key is not valid.
Can anybody help me ?
With regards
Hi, you probably have entered the values into the wrong variables. Try rotating them and see if you end up with a valid license key.
Awesome work.
Worked great on my TX1320 running iRMC S5.
Hello,
I cannot manage to do it.
I have a TX1320 M3 S4 without any license.
Is it anyone willing to guide me step by step?
Thanks in advance.
There is already a PoC, you just have to fill in three 16 byte values, which you can get from a hexdump tool. The steps are pretty clearly outlined in the post.
You can always buy a license from a Fujitsu reseller if you cannot figure it out.
Gentlemen, I am infinitely far from such things. But I bought a TX1330M1 and want to enable KVM. Can you help?
I can recommend reading the post and trying it yourself. The post explains pretty well what you need to do (fill in three 16 byte values in the python PoC). As the comments from other people say, it is not too hard, a few hours of work at most.
TypeError: ‘iv’ is an invalid keyword argument for this function
If iv removed, license key seems invalid
You may want to try `pip install pycryptodome`
Thanks, great work
with your post and some creativity it’s easy to figure it out what you have to do
WOW!
Even only a windows-machine on hand I got it working ON THE FIRST ATTEMPT!
With FireTigers hint for sure!
onworks linux system and a cloud space got me the lib and the remaining part was a hex editor and the mentioned hint!
Thanks!
P.S.: I don’t really need the license, but wanted to know, if I’m able to get it. My ambition was awakened….
BTW: what is this eLCM?
I realised the link to eLCM in the post no longer works, so here is a copy from the Internet Archive: https://web.archive.org/web/20220813122005/https://techcommunity.ts.fujitsu.com/en/servers/d/uid-33f876db-7e84-f041-8502-6f0188330448.html
In short: eLCM is a way to centrally manage firmware updates on a fleet of servers. You need additional software to host the update packages that iRMC will download and store on a local micro SD card. eLCM is not something a homelab user will care about.
Big thanks Martin! Took me few hours to figure all out, but absolutely worth the time. Not only because of the key, but for the inisght of reverse engineering for noobs 🙂
Hal Martin thank you very much!!
All works fine on S4(PRIMERGY TX2540 M1) and S6 (PRIMERGY TX1320 M5)
Hi,
i could only activate KVM.
KVM_Media and KVM_Media_eLCM are not working.
TX1320 M3 iRMC S4 FW 9.69F
Thanks Martin!
Primergy TX1320 M3 iRMC S4 FW 9.69F
KVM_Media and KVM_Media_eLCM are also working if -t RX is used
THX!
By the way – installing Ghidra was too laborious for me.
This online Tool also did the job: https://netdis.org/
Just upload your file and you’re good to go.
A simple hexdump tool is sufficient to obtain the necessary values. You do not need Ghidra for that. I have edited the post with this note.
Installing Ghidra is only suggested if people also wanted to reverse engineer the license validation.
I see your comment about using ChatGPT to “improve” the PoC. You are welcome to post this elsewhere, I will not put ChatGPT-derived code (especially lacking attribution) here.
Hi, interesting article. I have one question how to start the whole process? I mean about getting into firmware, its is possible via ssh? I logged in but that is no regular linux shell.
Best regards
I am already so close. I found lkeyInitCipherKey, HMAC I have these characters \00 \99 etc. But I don’t have “decrypt_with_license” in my file and I don’t really know how to find the
HMAC_MSG = b”” * 4
AES_IV = b””
Hmm… what I do wrong?
all the best
Arek
You do not need to use a disassembler for this, any hexdump utility will suffice. Look at the censored sections of the Ghidra hexdump screenshot and this comment.
Thanks! Working on RX1330M5 (S6)
iRMC S4 Firmware version: “8.43F”
iRMC S4 SDRR version: “3.12 ID 0452 TX1330M2”
System type: “PRIMERGY TX1330 M2”
Chassis type: “TX1330M2FA”
Tried with latest D3373_09.69F_sdr03.14 (24/02/2022) and then my own D3373_08.43F_sdr03.12 (01/07/2016)
9.96F contains /usr/local/lib/libfts_license.so.1.12.1
8.43F contains /usr/local/lib/libfts_license.so.1.6.0
followed the blurred screenshot and found it in 9.96F extracted and used the POC to generate the keys. Din’t work. found the same in 8.43F too. am I missing something? couldn’t follow firetiger’s comment.
Thank you!
Worked on Fujitsu C780 Workstation. iRMC S5.
Example license and serial at the beginning of the article helped a lot to discover correct place for each of 16 byte values.
PoC script changed to:
“from Cryptodome.Cipher import AES”
Works in U24.04, doesn’t work in Debian 12.
Thank you all for the hints 🙂
Greetings,
A.
I can confirm that this work fine on TX1320M2,M3 and M4. Its maybe worth noticing, that in the blurred screendump from Ghidra, you will see first 16 blurred characters, and then another 2×16 (32 characters), all together 3×16 blurred characters. These are the ones you should use for HMAC_KEY , HMAC_MSG and AES_IV. Now, the clue is which one goes where. Take each of those 16 characters strings, and convert them (with an online tool) from hex to text, one of the strings will make more “sense” than the other two. That string is the one you use in HMAC_MSG. Then it’s easy to find witch is HMAC_KEY and which is AES_IV.
This approach doesn’t work for old iRMC S2, unfortunately
Hi there!
I’m searching for the Library ‘/usr/local/lib/libfts_license.so.1.12.1.’ as it’s discribed in Hal Martin’s Article:
“I will not be disclosing Fujitsu’s HMAC key and AES IV here, but suffice to say you can download and unpack the iRMC firmware from Fujitsu and find the values in /usr/local/lib/libfts_license.so.1.12.1. ”
Where can I find it? I downloaded two versions of the IRMC-Firmware and had done this steps:
1. Download ‘FTS_RX300S8D2939iRMCKronos4FirmwareUpdatefo_RX300S80962Fsdr0374_1238981.BIN’
2. binwalk -e FTS_RX300S8D2939iRMCKronos4FirmwareUpdatefo_RX300S80769Fsdr0371_1119542.BIN
3. Tried to find ‘/usr/local/lib/libfts_license.so.1.12.1’ but I’ve only this files under ‘extractions’ :
https://paste.xinu.at/w1o/
Hi fluffy-bunny,
U need the tftp bin: 1238981. Then binwalk -e.
Note: u need cramfsck (from cramfs-tools or similar depending on your OS). For example in newer Ubuntus it is removed so download the source (only one c file) and compile it:
git clone https://github.com/davidribyrne/cramfs.git
make, make install
In this case you need zlib1g zlib1g-dev in Ubuntu.
After binwalk you have a _FTS_RX300…extracted directory where you can find the lib.
Use hexdump -X to dump the file and u will be able to find what you want 🙂 The image and the python code will help you.
PRIMERGY RX2540 M4 S5 work completed.
iRMC FW:03.61P_sdr03.87 boot: Ver 1.20P
Thank you all.
That permutation of the variables though…
Thanks for providing the example chassis value to check my efforts.
Hi Everyone!
Martin, thanks for this article.
I was able to get libfts_license.so.1.12.1 from RX1330M2_09.69F_sdr03.08.bin but the file is only 10’568 bytes and it has 139 lines only. Why so small? No address like 00012020.
Hello, thank you for great work!
Another detail to share: if you have only the motherboard, not whole server, after NVRAM clear your server’s serial number will be gone, only motherboard serial number left. Fujitsu manintenance manual says:
“The front panel module contains the Chassis ID EPROM that contains system information like server name and model, housing type, serial number and manufacturing data.”
So in case of replacing a system board in a real server, the serial number is automatically restored from front panel module, but in my case I have just the D3373-A1 motherboard, no front panel, so in system overview tab of iRMC I see:
System Type: – unknown –
Chassis Type: – unknown –
Serial: – unknown –
In such case, the string “- unknown -” appears to be the serial number, and a license generated for this serial works!