We’ve looked at how to setup libvirt for encrypted remote access using a SASL file database to authenticate users.
But, wouldn’t it be nice if we could integrate libvirt users into LDAP, like we did previously with Jenkins and Mediawiki? Doing so would give you the SSO benefits of Kerberos, and the security and policy features of FreeIPA.
To get started, we need to install some packages on the libvirtd server and the client where you’ll be running virsh or virt-manager.
Debian:
$ sudo apt-get install libsasl2-2 libsasl2-modules-gssapi-mit
CentOS/RedHat:
$ sudo yum install cyrus-sasl cyrus-sasl-gssapi
Arch Linux:
$ sudo pacman -S libsasl cyrus-sasl cyrus-sasl-gssapi
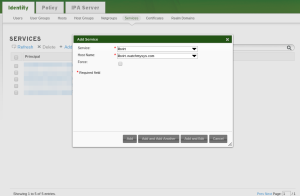
Next we need to create a service principal in LDAP for libvirt, and export it to a keytab which we’ll install on the libvirtd server. In the FreeIPA admin, navigate to: Identity -> Services -> Add
The service is “libvirt” and the Host Name is the server running libvirtd. In this example the principal would be “libvirt/[email protected]”
You can verify this by running ipa service-show on the IPA server:
$ ipa service-show libvirt/libvirt.watchmysys.com Principal: libvirt/[email protected] Keytab: True Managed by: libvirt.watchmysys.com
Once you’ve created the principal it needs to be exported to a keytab which will be installed on the libvirtd server:
ipa cert-request --principal=libvirt/libvirt.watchmysys.com libvirt.keytab
The libvirt.keytab file needs to be copied to /etc/libvirt/krb5.keytab the libvirtd server with permissions 0600.
Now we need to change SASL to authenticate using Kerberos, instead of the file based authentication we had before.
$ sudo vi /etc/sasl2/libvirt.conf mech_list: gssapi keytab: /etc/libvirt/krb5.keytab
Ensure that there are no other mechanisms defined in mech_list and that sasldb_path: is commented out.
Now if you have a valid ticket on your client you should be able to login using virsh or virt-manager without having to type in a username or password.
Before logging in to libvirtd:
client $ klist Ticket cache: FILE:/tmp/krb5cc_1000 Default principal: [email protected] Valid starting Expires Service principal 10/27/2014 20:06:48 10/28/2014 20:06:45 krbtgt/[email protected]
Open virt-manager or use virsh to connect to the hypervisor:
client $ virsh -c qemu+tls://libvirt.watchmysys.com/system list Id Name State ---------------------------------------------------- 1 debian7 running 2 centos7 running 3 arch2014.08 running 4 opensuse running 5 xbuntu1404 running 6 windows7 running
After logging in to libvirtd:
client $ klist Ticket cache: FILE:/tmp/krb5cc_1000 Default principal: [email protected] Valid starting Expires Service principal 10/27/2014 20:06:48 10/28/2014 20:06:45 krbtgt/[email protected] 10/27/2014 20:06:53 10/28/2014 20:06:45 libvirt/[email protected]
Nice.
Troubleshooting
Failed to start SASL negotiation: -4 (SASL(-4): no mechanism available: No worthy mechs found)
Check that you have the proper sasl gssapi packages installed on both the client and the server.