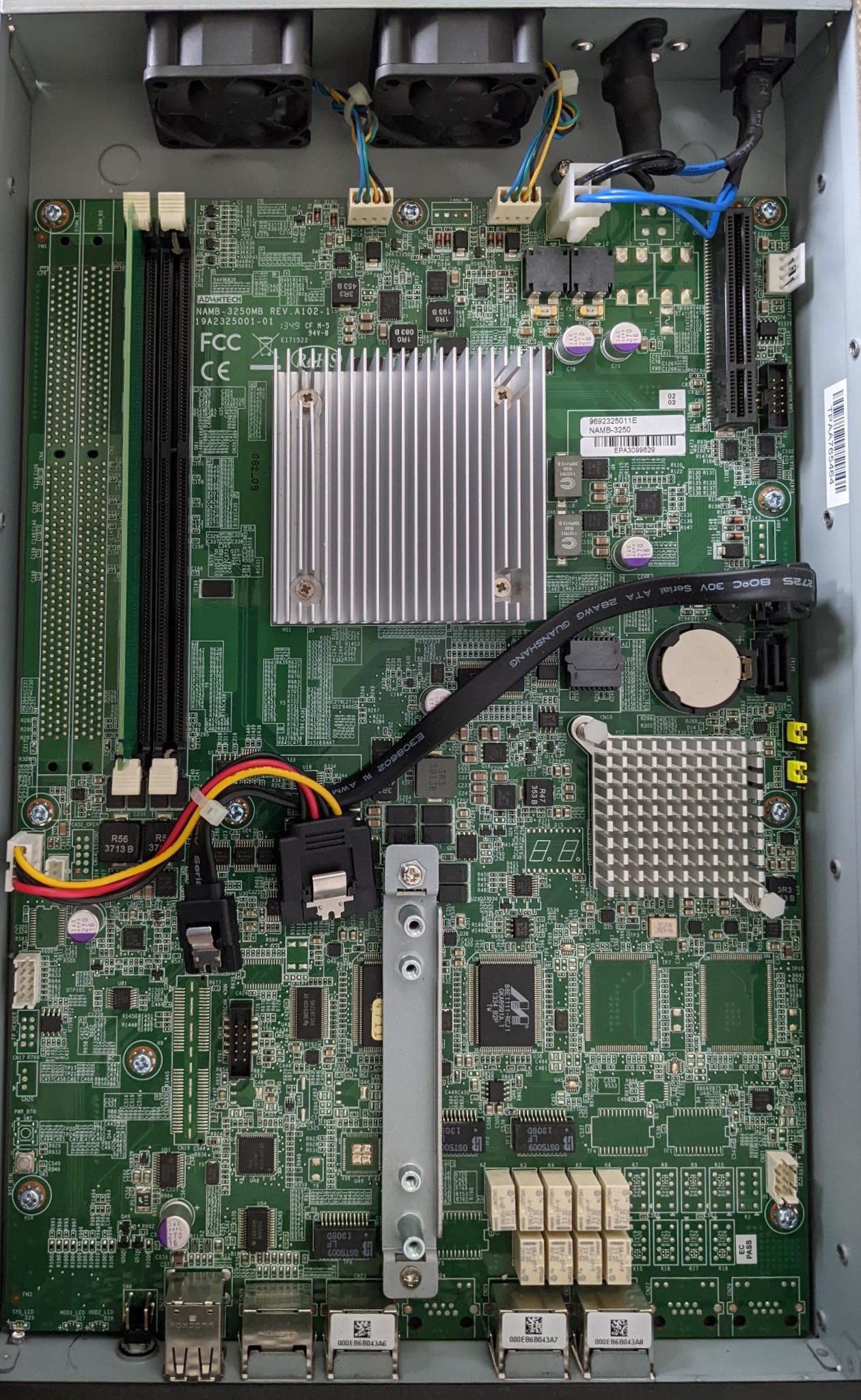
The Riverbed SteelHead are a series of bandwidth optimization appliances that can typically be found for a reasonable price on eBay. Today we are looking at the Riverbed CX 255 (36€ from eBay.de), a small unit with 3 Ethernet interfaces.

Powering the CX 255 is an Intel Celeron 725C (1C2T) soldered to the NAMB-3250MB motherboard, along with with 2GB of DDR3-1333 unbuffered ECC. You will not win any benchmarks with this CPU.
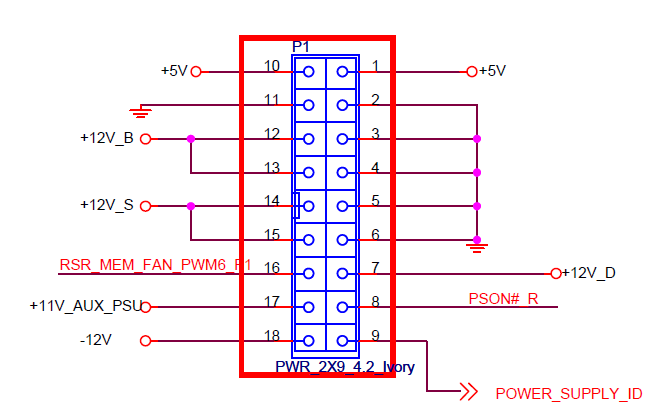
The CX 255 consumes 20W idle, and is powered by an external 12V 7A power supply (5.5×2.5mm, center positive).
Running powertop --auto-tune sadly does nothing to the reduce power consumption. It appears to the primary reason for this is the high power consumption of the DH89xxCC chipset used
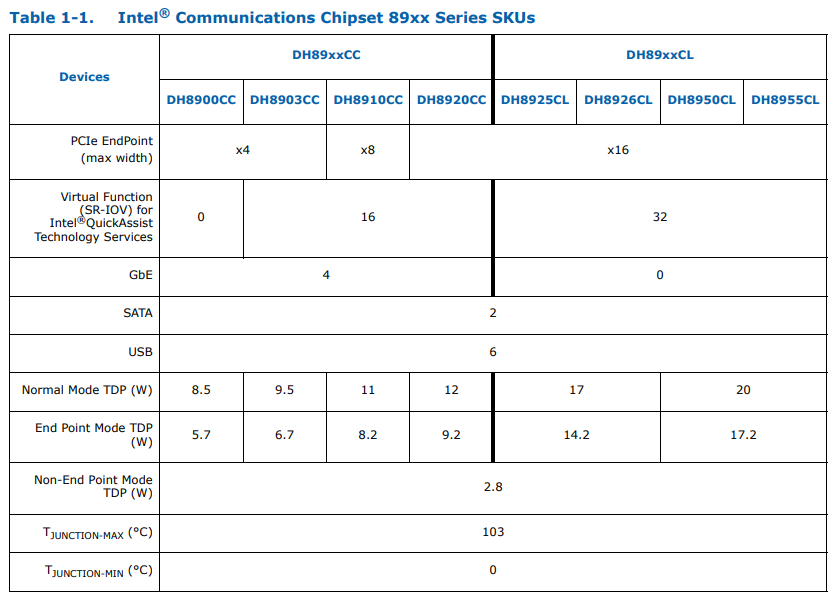
DH89xxCC chipset features and TDP (PDF)
The console port uses the Cisco rollover cable pinout, and operates at 115200n8. The two 40mm PWM fans run at around 5000RPM, and while not they do not scream as some 1U servers do, they are clearly audible from several meters away.
00:00.0 Host bridge: Intel Corporation 2nd Generation Core Processor Family DRAM Controller (rev 09) 00:01.0 PCI bridge: Intel Corporation Xeon E3-1200/2nd Generation Core Processor Family PCI Express Root Port (rev 09) 00:1c.0 PCI bridge: Intel Corporation DH89xxCC PCI Express Root Port #1 (rev 08) 00:1d.0 USB controller: Intel Corporation DH89xxCC USB2 Enhanced Host Controller #1 (rev 08) 00:1f.0 ISA bridge: Intel Corporation DH89xxCC LPC Controller (rev 08) 00:1f.2 SATA controller: Intel Corporation DH89xxCC 4 Port SATA AHCI Controller (rev 08) 00:1f.3 SMBus: Intel Corporation DH89xxCC SMBus Controller (rev 08) 00:1f.6 Signal processing controller: Intel Corporation DH89xxCC Thermal Subsystem (rev 08) 00:1f.7 System peripheral: Intel Corporation DH89xxCC Watchdog Timer (rev 08) 01:00.0 Co-processor: Intel Corporation DH89XXCC Series QAT (rev 21) 01:00.1 Ethernet controller: Intel Corporation DH8900CC Series Gigabit Network Connection (rev 21) 01:00.2 Ethernet controller: Intel Corporation DH8900CC Series Gigabit Network Connection (rev 21) 02:00.0 Ethernet controller: Intel Corporation I210 Gigabit Network Connection (rev 03)
There are also the CX 570 and CX 770, which appear quite similar from the exterior. The CX 570 and CX 770 have three additional Ethernet interfaces and better CPUs. According to this document (PDF) the CX 570 has an Intel Pentium B925C while the CX 770 has an Intel Xeon E3-1125C v2.
From the lspci output on the CX 255 and the board layout, I assume that the CX 570/770 has an additional I210 controller and the remaining 2 Ethernet PHYs from the DH8900CC populated. I anticipate that the idle power consumption is similar to that of the CX 255.
Here is the lspci output from the CX 770:
00:00.0 Host bridge: Intel Corporation 3rd Gen Core processor DRAM Controller (rev 09) 00:01.0 PCI bridge: Intel Corporation Xeon E3-1200 v2/3rd Gen Core processor PCI Express Root Port (rev 09) 00:1c.0 PCI bridge: Intel Corporation DH89xxCC PCI Express Root Port #1 (rev 08) 00:1c.1 PCI bridge: Intel Corporation DH89xxCC PCI Express Root Port #2 (rev 08) 00:1d.0 USB controller: Intel Corporation DH89xxCC USB2 Enhanced Host Controller #1 (rev 08) 00:1f.0 ISA bridge: Intel Corporation DH89xxCC LPC Controller (rev 08) 00:1f.2 SATA controller: Intel Corporation DH89xxCC 4 Port SATA AHCI Controller (rev 08) 00:1f.3 SMBus: Intel Corporation DH89xxCC SMBus Controller (rev 08) 00:1f.6 Signal processing controller: Intel Corporation DH89xxCC Thermal Subsystem (rev 08) 00:1f.7 System peripheral: Intel Corporation DH89xxCC Watchdog Timer (rev 08) 01:00.0 Co-processor: Intel Corporation DH89XXCC Series QAT (rev 21) 01:00.1 Ethernet controller: Intel Corporation DH8900CC Series Gigabit Network Connection (rev 21) 01:00.2 Ethernet controller: Intel Corporation DH8900CC Series Gigabit Network Connection (rev 21) 01:00.3 Ethernet controller: Intel Corporation DH8900CC Series Gigabit Network Connection (rev 21) 01:00.4 Ethernet controller: Intel Corporation DH8900CC Series Gigabit Network Connection (rev 21) 02:00.0 Ethernet controller: Intel Corporation I210 Gigabit Network Connection (rev 03) 03:00.0 Ethernet controller: Intel Corporation I210 Gigabit Network Connection (rev 03)
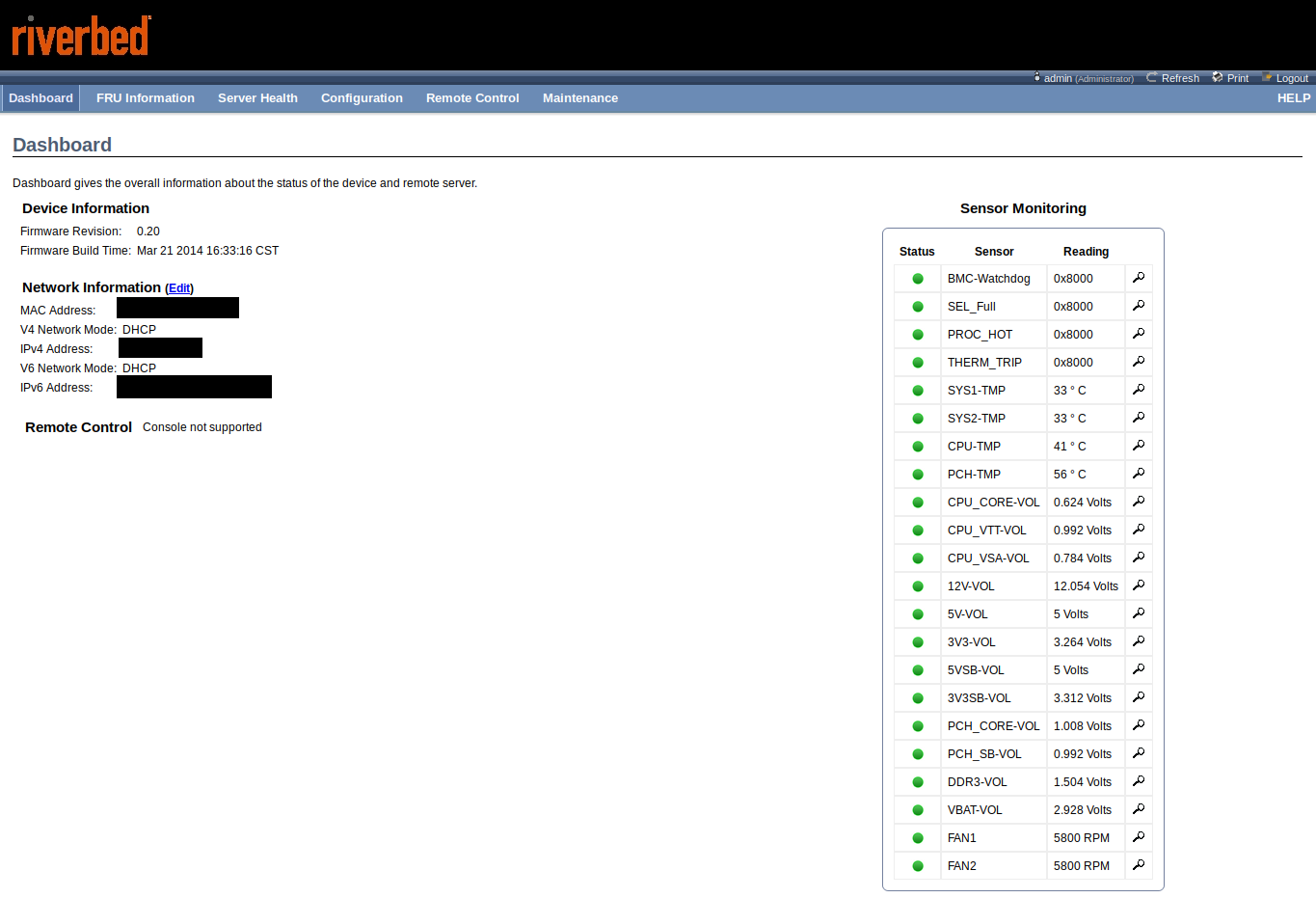
The CX 770 also includes minimal lights out management (Aspeed AST1050 BMC), which can be configured to share the PRI ethernet interface. The BMC only provides remote power control and sensor readings, there is no support for KVM or serial console redirection.