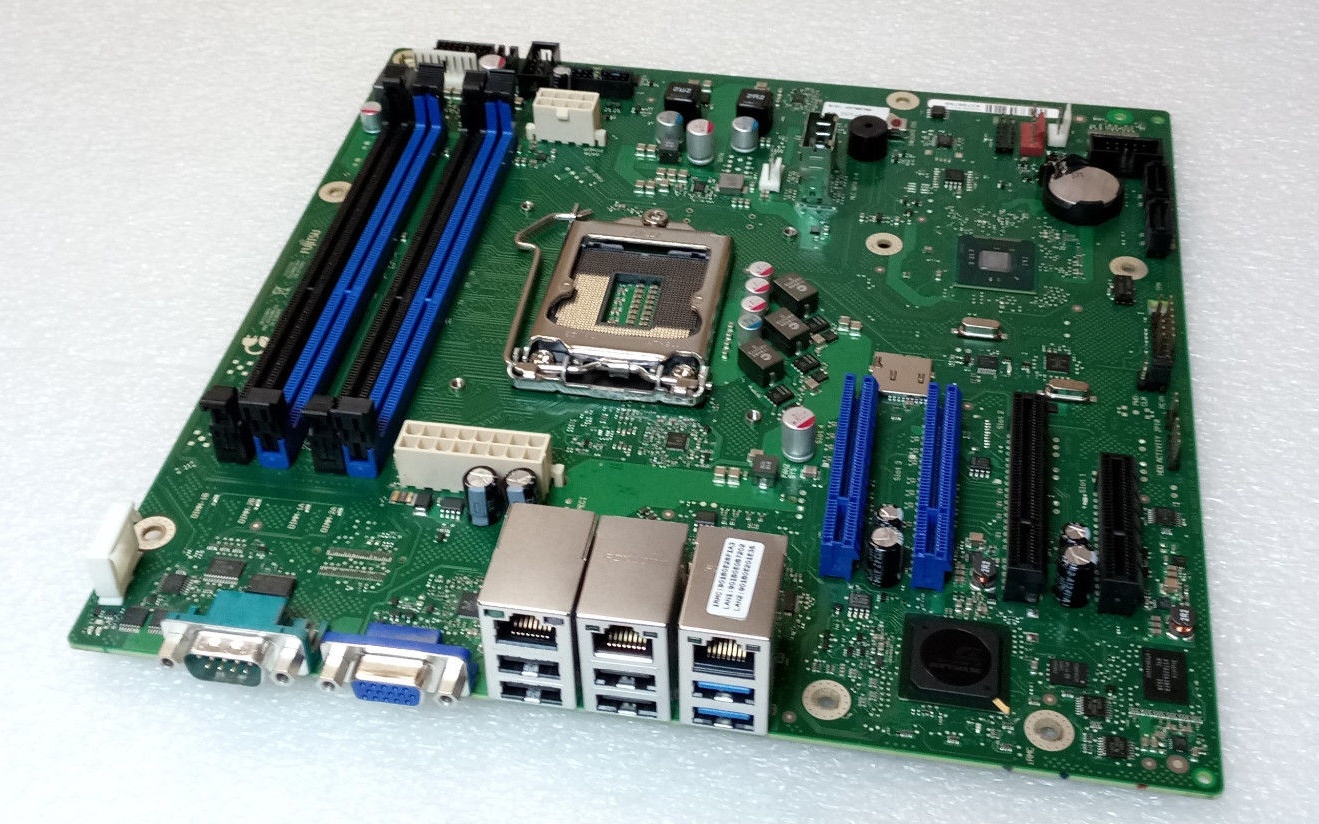
The SuperMicro X10SLE-F is nice, but it has very limited expansion; no PCIe slots and the MicroLP adapters with SFP+ are insanely expensive. Fujitsu motherboards, in the EU, are quite cheap (33€ on eBay) and I have never owned a Fujitsu system before, so I thought I would give it a try.
The first order of business, since I bought a bare motherboard, is to power it from an ATX power supply. Luckily for me, other people have determined the 16-pin power supply pinout:
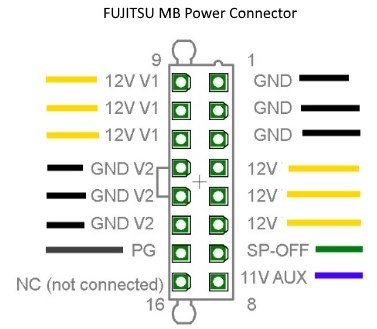
Side note: this appears to be a common power supply connector for Fujitsu motherboards with a 16-pin power connector. The Celsius W520 uses the same pinout.
The 12V rail appears to go directly to the PCIe slots and is completely isolated from 12V V1.
If the ambient temperature sensor is absent, iRMC considers the system in an error state. The Global Error/CSS lights are flashing and the fans run at full speed (100% PWM).
Unfortunately the ambient temperature sensor is integrated into the front-panel assembly (c26361-k644-c550), which I don’t have:

I couldn’t locate the technical manual for the TX140 S2 (D3239), but technical manual of the TX140 S1 (D3049) has the following to say:
Measurement of the processor and the system internal temperature by an onboard temperature sensor, measurement of the ambient temperature by a I²C temperature sensor.
System board D3049 for PRIMERGY TX140 S1 / TX120 S3 – Technical Manual
I am unaware of any publicly available pinout of the 16 pin front-panel header (2×8, 2.0mm spacing), so I reverse engineered it:
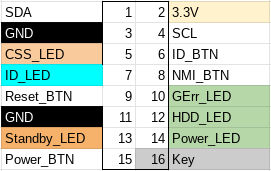
In table format:
| Pin | Description | Pin | Description |
|---|---|---|---|
| 1 | SDA (serial data) | 2 | 3.3V |
| 3 | Ground | 4 | SCL (serial clock) |
| 5 | CSS LED positive (Customer self service) | 6 | ID button |
| 7 | ID LED+ (anode) | 8 | NMI button |
| 9 | Reset button | 10 | Global Error LED+ (anode) |
| 11 | Ground | 12 | HDD activity LED+ (anode) |
| 13 | Standby LED+ (anode) | 14 | Power LED+ (anode) |
| 15 | Power button | 16 | Key (pin absent) |
We can confirm the I²C pins with a logic analyzer:
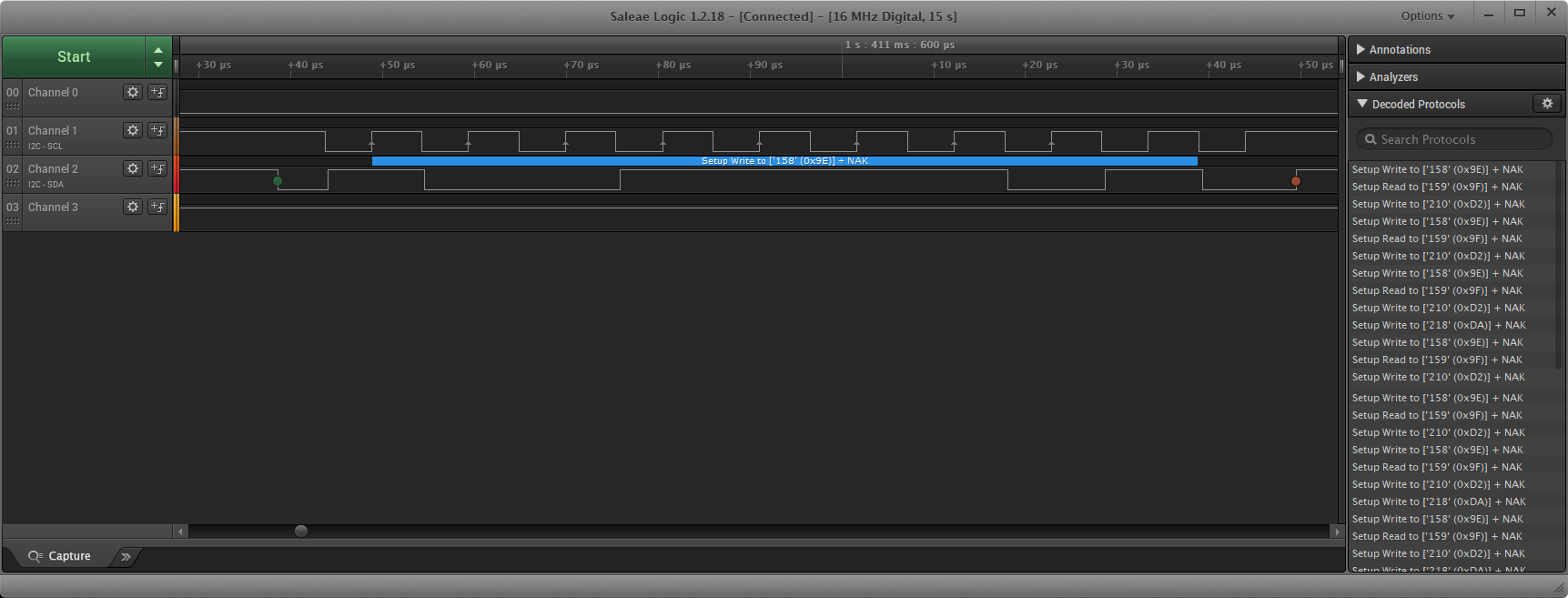
Now unfortunately, there are no high resolution photos of the front-panel PCB, so it’s not possible to easily determine which I²C temperature sensor is being used.
There is a photo of a Fujitsu RX300 front-panel with a failed temperature sensor, but that is only enough to allow us to guess the chip model as the Texas Instruments LM75.

We can also guess the I²C address from the RX300 front-panel: all 3 address lines should be tied to VCC.
Now with the sensor connected to the front-panel connector using the pinout above, it is time to find out if Fujitsu used the same ambient temperature sensor on the RX300 and TX140 S2, and if I guessed the I2C address correctly.
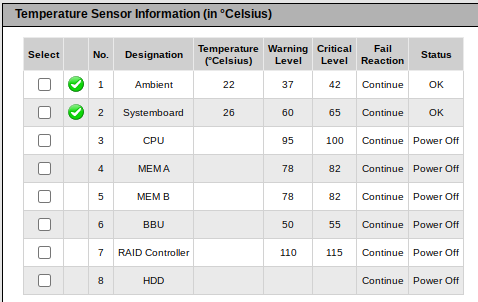
There is a chassis IDPROM also in the front panel assembly, which from the iRMC log appears to store a backup of the BIOS parameters after successful POST. I consider the IDPROM somewhat optional, as iRMC does not consider it a critical component in terms of server functionality.
First impressions are good, power consumption is very low, though not as low as the X10SLE-F. Idle power consumption in Linux is under 20W with an E3-1220 v3 and 16GB of PC3L-12800E.
lspci output:
00:00.0 Host bridge: Intel Corporation Xeon E3-1200 v3 Processor DRAM Controller (rev 06)
00:01.0 PCI bridge: Intel Corporation Xeon E3-1200 v3/4th Gen Core Processor PCI Express x16 Controller (rev 06)
00:01.1 PCI bridge: Intel Corporation Xeon E3-1200 v3/4th Gen Core Processor PCI Express x8 Controller (rev 06)
00:14.0 USB controller: Intel Corporation 8 Series/C220 Series Chipset Family USB xHCI (rev 05)
00:19.0 Ethernet controller: Intel Corporation Ethernet Connection I217-LM (rev 05)
00:1a.0 USB controller: Intel Corporation 8 Series/C220 Series Chipset Family USB EHCI #2 (rev 05)
00:1c.0 PCI bridge: Intel Corporation 8 Series/C220 Series Chipset Family PCI Express Root Port #1 (rev d5)
00:1c.2 PCI bridge: Intel Corporation 8 Series/C220 Series Chipset Family PCI Express Root Port #3 (rev d5)
00:1d.0 USB controller: Intel Corporation 8 Series/C220 Series Chipset Family USB EHCI #1 (rev 05)
00:1f.0 ISA bridge: Intel Corporation C224 Series Chipset Family Server Standard SKU LPC Controller (rev 05)
00:1f.2 SATA controller: Intel Corporation 8 Series/C220 Series Chipset Family 6-port SATA Controller 1 [AHCI mode] (rev 05)
00:1f.3 SMBus: Intel Corporation 8 Series/C220 Series Chipset Family SMBus Controller (rev 05)
00:1f.6 Signal processing controller: Intel Corporation 8 Series Chipset Family Thermal Management Controller (rev 05)
03:00.0 VGA compatible controller: Matrox Electronics Systems Ltd. MGA G200e [Pilot] ServerEngines (SEP1) (rev 05)
03:00.1 Co-processor: Emulex Corporation ServerView iRMC HTI
04:00.0 Ethernet controller: Intel Corporation I210 Gigabit Network Connection (rev 03)I have requested the GPL source code of iRMC from Fujitsu, and if they get back to me with the source code I may have some interesting findings to share. Stay tuned…